Robust access controls are essential to prevent data leakage and meet compliance requirements. Two commonly used access control models are role-based and attribute-based access control. Both approaches have unique strengths and can provide layers of defense when used together.
This article explores key differences between RBAC and ABAC and discusses how you can combine both of these access control methods by covering the following topics:
What is RBAC
Role-based access control (RBAC) restricts access based on a user’s role within the organization. It aligns user roles and permissions so users can only access data necessary for their job duties.
For example, data analysts might have read-only access to analytical datasets while data engineers have broader permissions to ingest, transform, and load data into the lake.
What Does RBAC Protect Your Data From?
RBAC protects against the risks of providing overly permissive access. By limiting data access to minimize privilege, RBAC:
- Prevents privileged users like admins from accessing sensitive data unnecessary for their roles.
- Stops users from accessing data irrelevant to their jobs, reducing the risk of intentional and unintentional data misuse or leakage.
- Supports compliance by restricting unauthorized data access and modifications.
- Reduces attack surface by limiting access to only authorized users.
Proper RBAC configurations limit standing access to only systems users need for their current role’s duties. This supports the principle of least privilege and minimizes unnecessary data exposure. RBAC can further protect data with fine-grained roles defined.
Granting User Data Access with RBAC
With RBAC, IT administrators create roles that represent common user duties. For example, roles like “analyst,” “engineer,” and “data scientist.”
Admins then assign these roles to users based on their responsibilities. Roles have pre-defined permissions to access specific resources like files, tables, and views.
For example, the “analyst” role may have read-only access to customer data for reporting. The “engineer” role may have broader access to ingest and transform raw data.
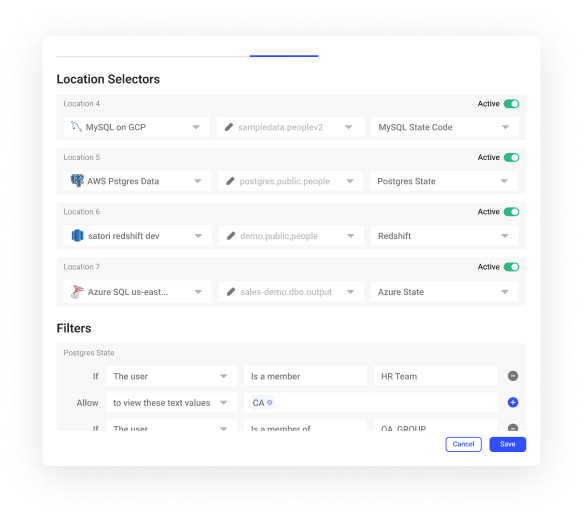
Administration of RBAC
Administering RBAC requires actively managing user roles and permissions as needs change. The main administrative tasks include:
- Creating new roles to represent new job functions.
- Updating role definitions when duties change.
- Deleting old roles that are no longer needed.
- Assigning users to appropriate roles based on their responsibilities.
- Revoking role assignments when users switch jobs.
- Defining and maintaining role permissions through ACLs.
- Periodically reviewing role definitions and assignments for proper alignment.
A key advantage of RBAC is the ability to manage access for many users under a role. Making the changes role-by-role, is time-consuming with fine-grained roles. Automated provisioning and de-provisioning based on HR system data can help streamline ongoing RBAC administration.
What is ABAC?
Attribute-based access control (ABAC) bases access decisions on a user’s attributes rather than only their role. Attributes may include the user’s department, title, project, and other identity-related characteristics.
For example, ABAC could restrict access to a database table to users from the payroll department, regardless of their specific role. This provides more nuanced and flexible access controls tailored to dynamic user needs.
How Does ABAC Protect Your Data?
By controlling access based on user attributes, ABAC secures data by:
- Restricting access to specific attribute combinations, preventing standing excessive access as user responsibilities shift,
- Adapting permissions automatically as user attributes change through transfers etc.
- Granting time-bound access only while user attributes require it limiting access to contractors and other temporary users.
- Detecting risky access attempts based on identity traits.
- Providing dynamic access decisions tailored to the context instead of static role definitions.
- Continuously evaluating access to minimize standing permissions.
Assigning Access with ABAC
ABAC evaluates a user’s assigned attributes to determine access. Policies define which attributes warrant access to a resource.
For example, a policy may specify that only users from the ‘payroll’ department can access the ‘salary’ table. In this example, when Mike, who works in payroll, attempts access, ABAC checks his ‘department: payroll’ attribute and allows access. When Sarah, who works in sales attempts access, ABAC sees she lacks the ‘payroll’ attribute and blocks access.
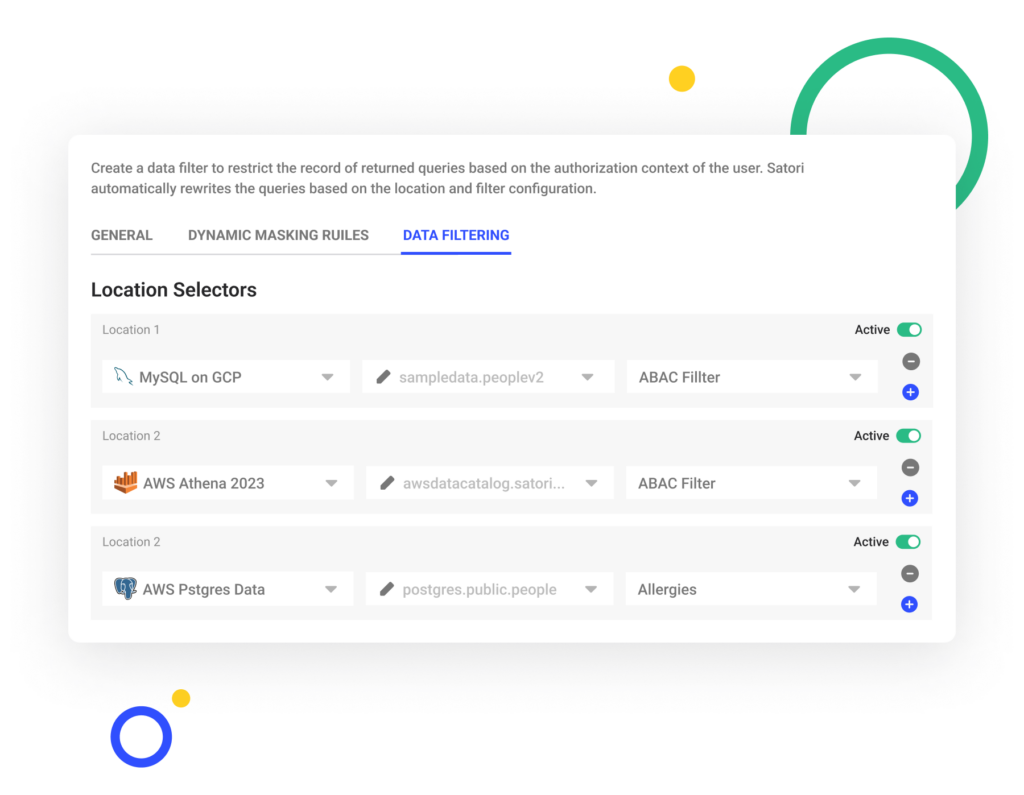
Administration of ABAC
Administering ABAC involves managing user attributes and writing access control policies based on those attributes. Key responsibilities include:
- Identifying meaningful user attributes like department, title, project, location, etc.
- Assigning user attributes through integration with HR and IT systems.
- Crafting access policies based on combinations of attributes.
- Analyzing access patterns and refining policies over time.
- Updating policies and attribute assignments as users change.
A major advantage of ABAC is the ability to write access rules one time rather than updating permissions user-by-user. But, formulating meaningful policies based on attributes requires significant upfront planning and analysis for effective ongoing administration.
Using a Hybrid Approach for Access Control
RBAC and ABAC offer complementary strengths when used together. RBAC provides the foundation of least-privilege access aligned to roles. ABAC adds dynamic controls to limit standing access and adapt to changing needs.
For example, RBAC could define an “analyst” role with access to reporting data while ABAC limits access to analysts in the payroll department.
A hybrid model combines attributes, roles, and rules to build flexible and nuanced access policies tailored to your data lake’s security needs. Data access platforms like Ranger and Sentry support creating hybrid access models.
Start by defining key roles and common permissions with RBAC. Then layer on ABAC rules based on identity attributes, risk factors, or other contextual access requirements. Carefully plan role definitions and ABAC policies before implementation to maximize security and avoid disruptions.
Conclusion
Limiting data access through RBAC and ABAC protects your data from unauthorized access. RBAC aligns permissions with roles and responsibilities while ABAC adapts access based on user attributes. Using both access control systems together bridges their strengths to create nuanced, flexible access policies specific to your security needs. With proper access controls in place, you can unlock the full potential of your data to deliver analytical insights without putting sensitive information at risk.
Satori’s Data Security Platform provides both RBAC and ABAC, as well as self-service and just-in-time data access controls to secure your data access from a single platform.
To learn more about Satori’s Data Security Platform book a consulting call with one of our experts.



