Data Access Control
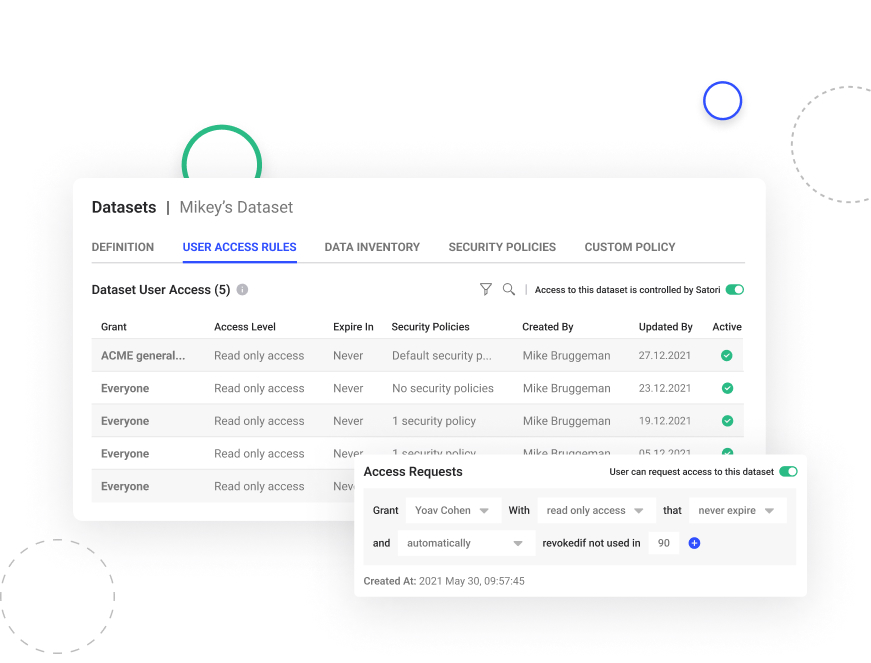
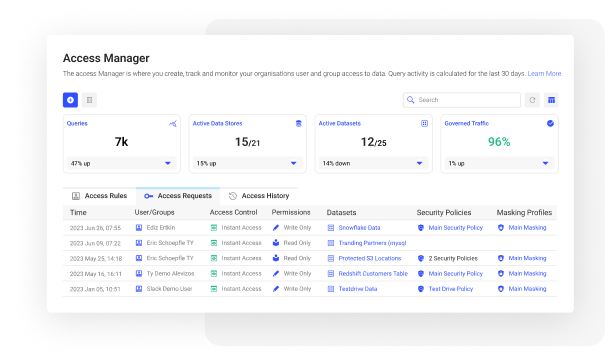
Single-Pane Access Management
Related blogs:
Managing Access to Data Just Got a Whole Lot Easier
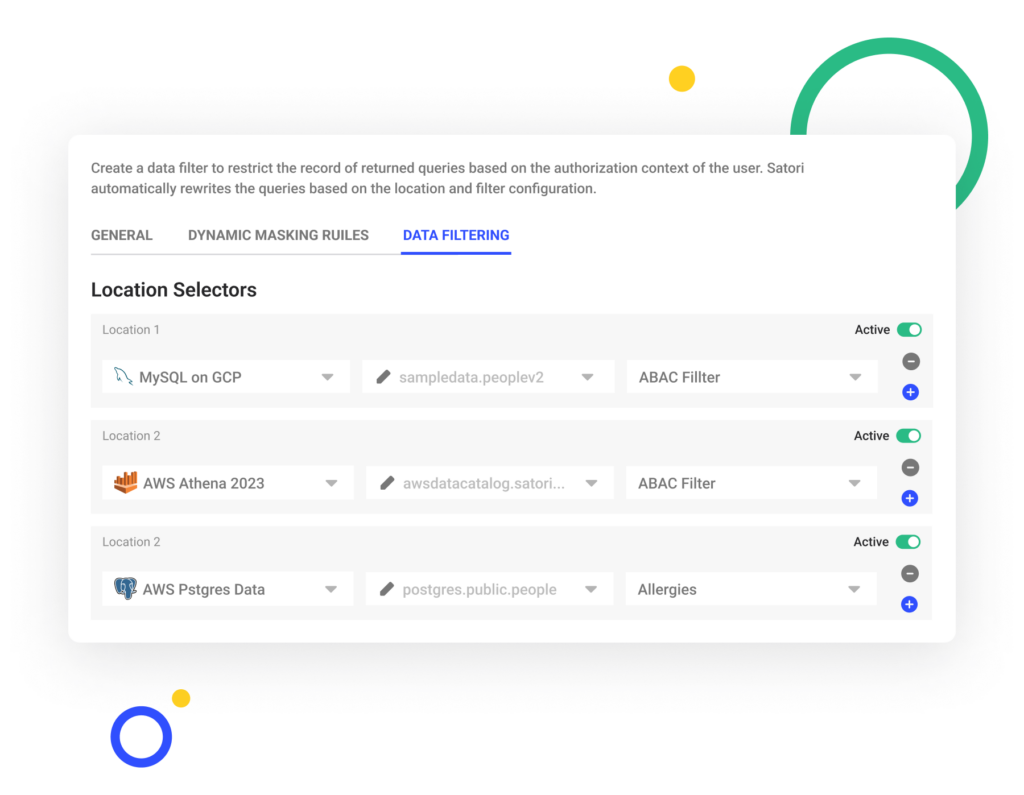
ABAC: Attribute-Based Access Control
Attribute-based access control allows you to set policies on attributes that can be based on user identity, connecting tool, and more.
Satori allows data owners to implement ABAC regardless of the data store technology and its native capabilities. Data owners have the ability to apply security policies such as restricting access to sensitive data from certain locations or locking in users to specific BI tools.
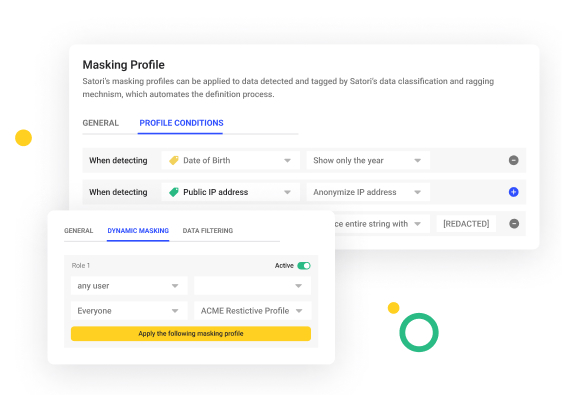
Dynamic Data Masking
Apply dynamic masking on thousands of tables in minutes. Masking policies are based on data types and identities, including RBAC and users; and are not reliant on specific locations.
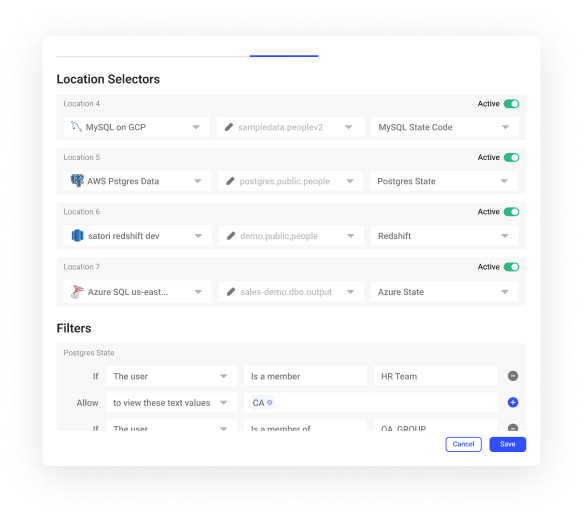
Row-Level Security
Access partial data from data tables, according to specific conditions. For example, each user should only be able to view customer data for their region.
Satori’s row-level security works across all of your data stores and is easy to configure without writing any code. It supports a multitude of row-level security and entitlement scenarios to ensure access control is easily applied.
Related blogs:
Simplifying Data Localization Requirements With Satori
Read More Here
Solution Brief
Satori’s Data Security Platform
Satori’s comprehensive Data Security Platform eliminates the complexity of managing access to sensitive data. Using data security automation streamlines secure access to data when and where it is needed (just-in-time) while consistently ensuring security policies are applied across all data platforms.

Case Study
Satori Helps Wealthsimple Secure Sensitive Data & Remain Compliant Without Sacrificing Growth
Satori helps Wealthsimple protect sensitive customer data in Amazon Redshift, using need-to-know access, without sacrificing hyper-growth.

Blog Post
How Automating Access to Data Enhances Customer Engagement & Trust
Automated access to data is designed to safeguard information from unauthorized access. But it’s not just about security, automated access to data also has the power to enhance customer engagement and build trust.




