In this chapter, we’ll take a deep dive into today’s leading cybersecurity frameworks and the ends they serve. The following topics will be covered:
Why are Cybersecurity Frameworks Important?
While the fragmented nature of the cybersecurity market serves the cat & mouse chase between attackers and guardians, the inevitable result is the existence of dozens of different cyber security vendors a midsize enterprise has to adopt and deploy across his supply chain and digital service delivery. This reality introduces significant complexity when it comes to running an effective enterprise information security program. Therefore, the number one purpose of Cyber security frameworks is to introduce standardization, best practices and structure around the technology implementation used for such programs.
What is an IT Security Framework?
An IT security framework is a collection of documents and procedures that a typical enterprise can use in order to implement an information security program and put a formal structure around the varying controls mentioned above. Such a framework will typically not specify tools or vendor selections.
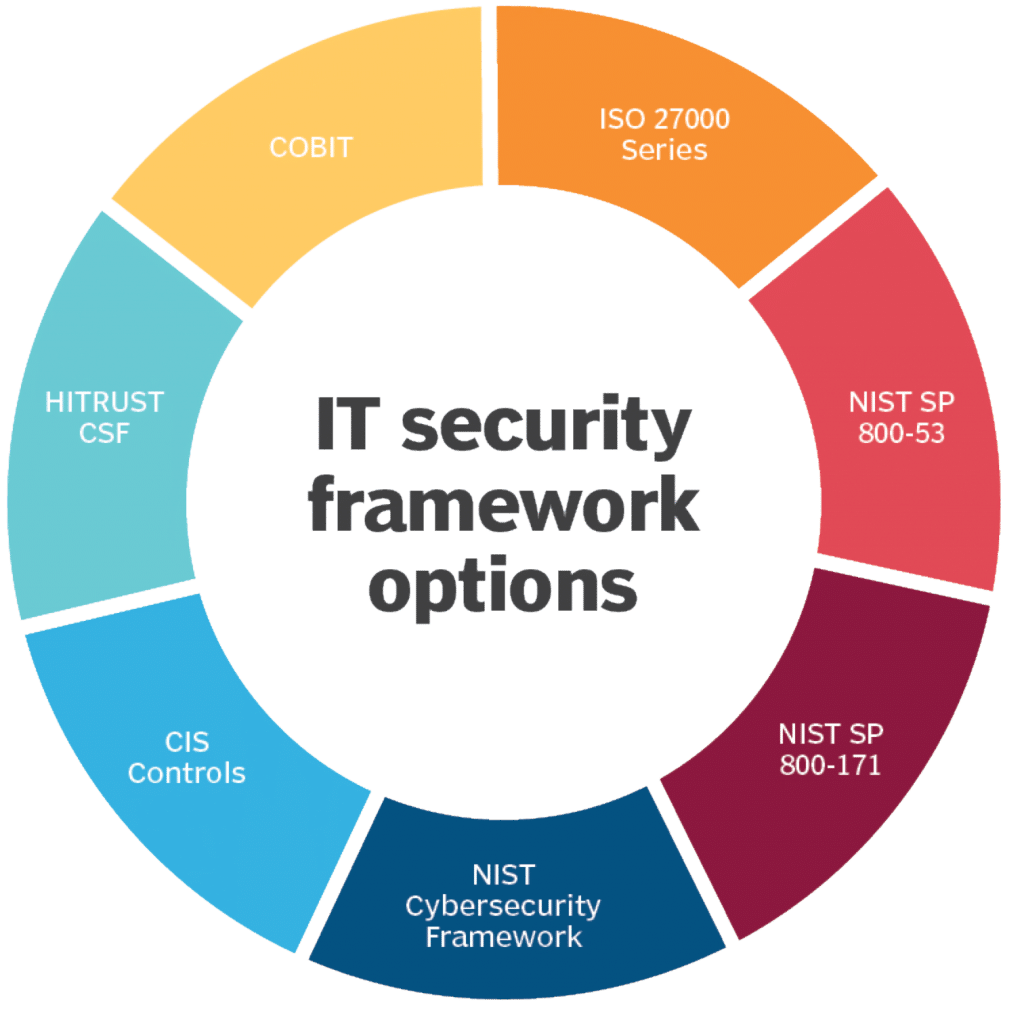
What are Common Cybersecurity Control Frameworks?
With the introduction of industry specific regulations such as PCI-DSS, HIPAA, SOX, Fedramp, (and others) which started in the mid 90s’, and the maturity of information security practices, we’ve seen organizations such as NIST, ISO and CSA build structure and framework around enterprise security best practices and forming a set of cyber security frameworks. Here’s a list of the most common Frameworks out there:

Understanding NIST CSF Security Controls
The NIST Cybersecurity Framework is organized in the following hierarchical way: 5 Core Function mapped to 23 Category broken down to 108 Sub categories in the following way (excluding sub categories):activities.
Function
Category
Identify
Asset Management
Business Environment
Governance
Risk Assessment
Risk Management Strategy
Supply Chain Risk Management
Protect
Identity Management and Access Control
Awareness and Training
Data Security
Information Protection Processes and Procedures
Maintenance
Protective Technology
Detect
Anomalies and Events
Security Continuous Monitoring
Detection Processes
Respond
Response Planning
Communications
Analysis
Mitigation
Improvements
Recover
Recovery Planning
Improvements
Communications
*The full details of NIST CSF including the breakdown to the 108 sub categories can be found here
Interesting to note that NIST subcategories also include an Informative Reference to other 6 security frameworks: CIS CSC, COBIT, ISA 62443, ISO/IEC 27001 and NIST 800-53 making it easier for enterprises integrate different frameworks in tandem.



