Audit & Monitoring
Satori centralizes all your data access logs in one place, adding additional metadata, such as applying detailed identity and security policies, helping you extract value from data access logs and meet and exceed your compliance and security requirements.
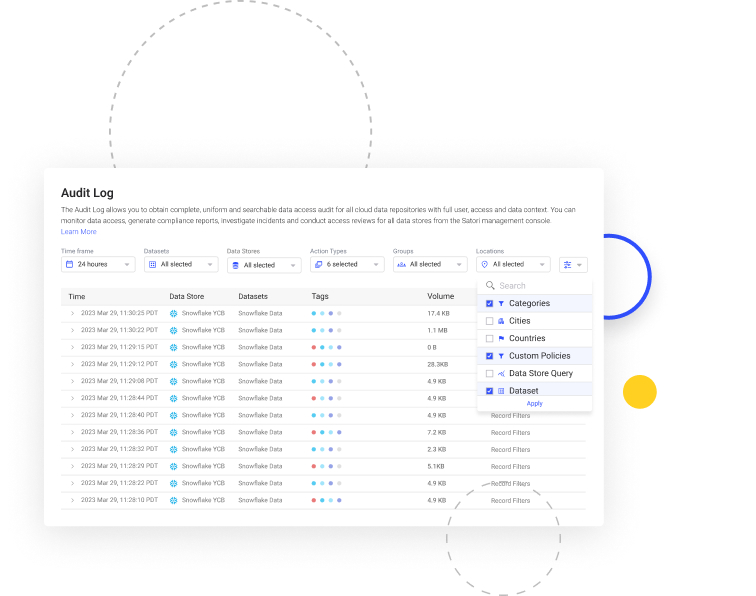
Universal Data Access Audit
Streamline maintaining, viewing, analyzing, and reporting data access logs across multiple data stores from a single location without any cumbersome setups.
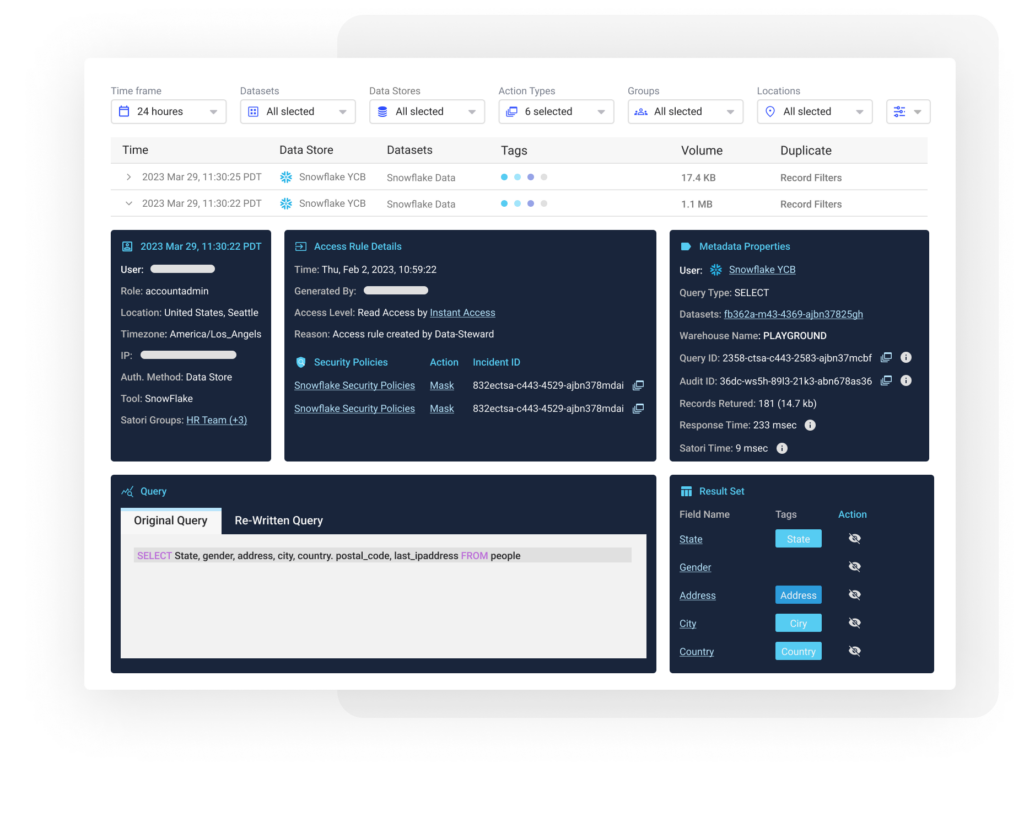
Understanding the Context of Data Access
Get the missing contextual information about data access from a centralized depository with enriched metadata about all data access, including identity data, types of sensitive data, and the application of any security policies.
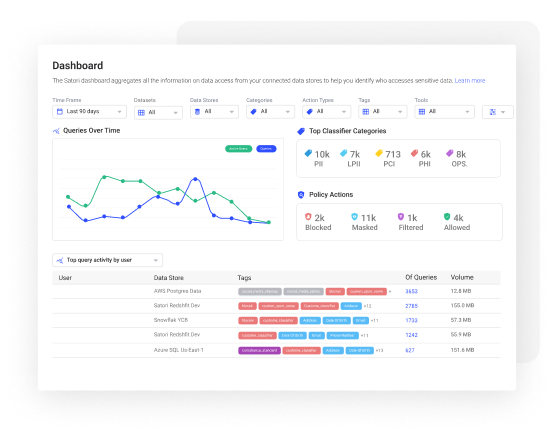
Analyze Enriched Audit Data at Scale
Create customized reports, identify behavior anaomlies, and use all data access logs from platforms like Splunk, Snowflake, DataDog or Elastic, and apply analytics directly on your data access metadata.
Know Who has Access to What
Scan all data permissions using Satori’s open-source UDPS (Universal Data Permissions Scanner) across all of your databases, data warehouses, and cloud data. Observing all permissions enables you to understand who has access to what data within your organization at all times.
Related blogs:
Posture Management
Read More Here
Solution Brief
Satori’s Data Security Platform
Satori’s comprehensive Data Security Platform eliminates the complexity of managing access to sensitive data. Using data security automation streamlines secure access to data when and where it is needed (just-in-time) while consistently ensuring security policies are applied across all data platforms.

Case Study
Satori Helps Wealthsimple Secure Sensitive Data & Remain Compliant Without Sacrificing Growth
Satori helps Wealthsimple protect sensitive customer data in Amazon Redshift, using need-to-know access, without sacrificing hyper-growth.

Case Study
Gong Automates Data Access Accelerating Time-to-Value Securely
Learn how Gong’s DevOps team uses Satori to control access to production data.




